The SSH protocol (also referred to as Secure Shell) is a method for reliable secure server remote login from one computer to another. It provides several alternative options for strong authentication, and it protects the communications security and integrity with strong encryption.
Change SSH Port
Open CWP panel in browser and login with admin account by using https://your_domain.com:2087 (2087 for secure login).
Click on services config and select SSH configuration under it.
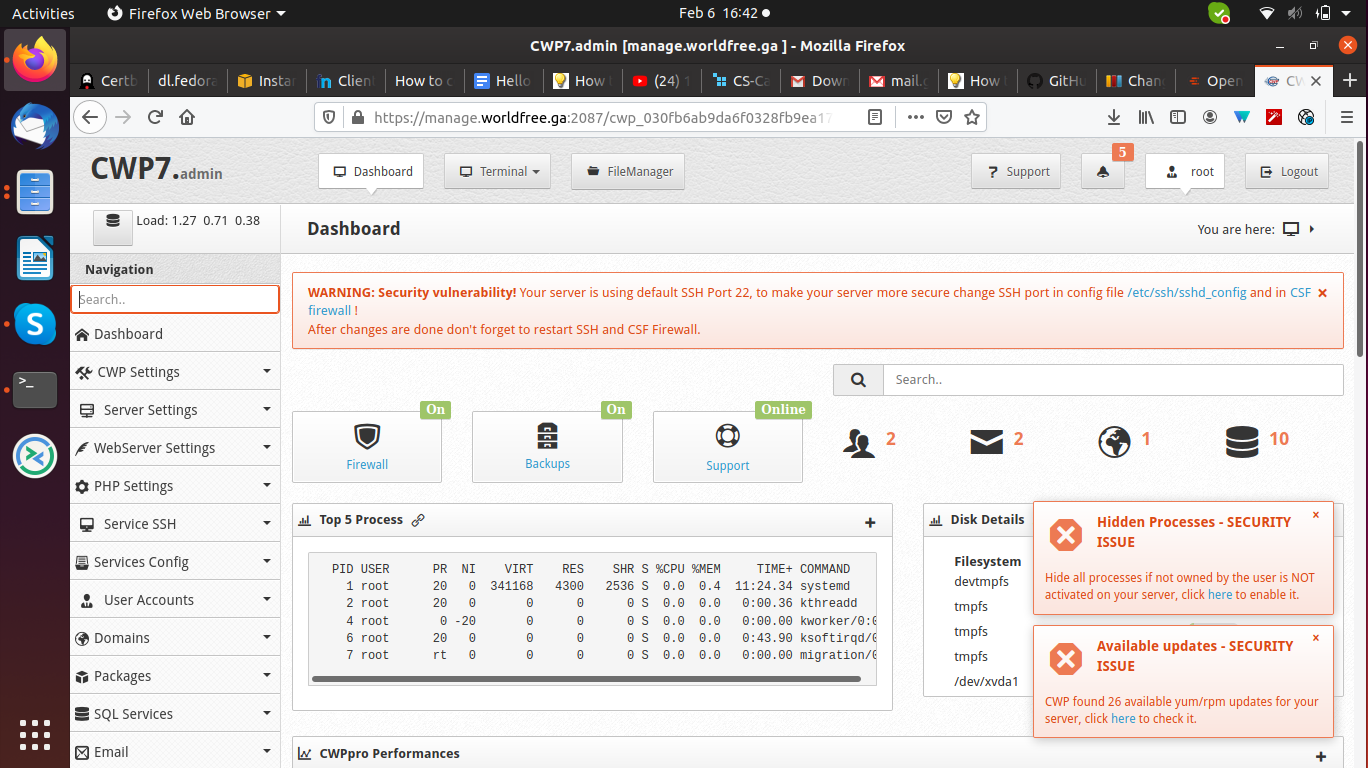
Port 22 is the default port on which SSH service listens to enhance the security you should change it.
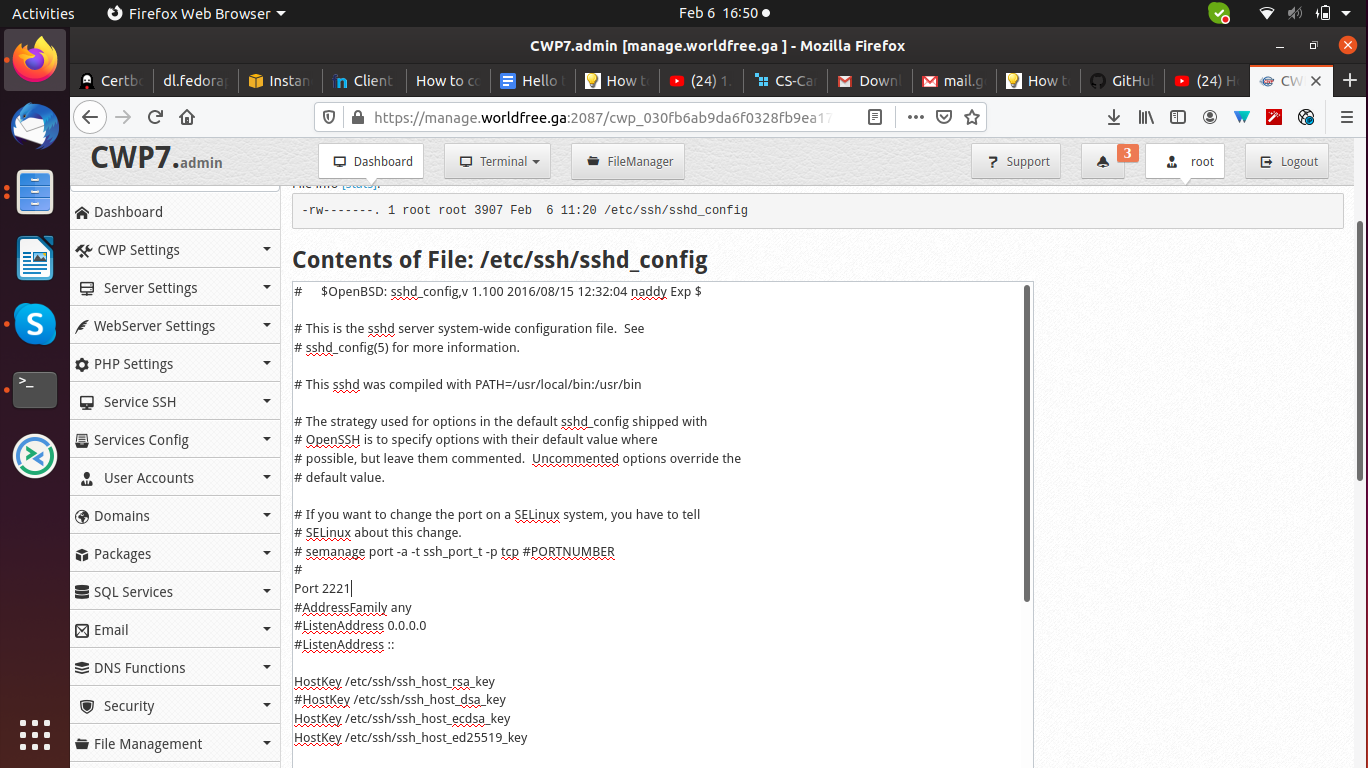
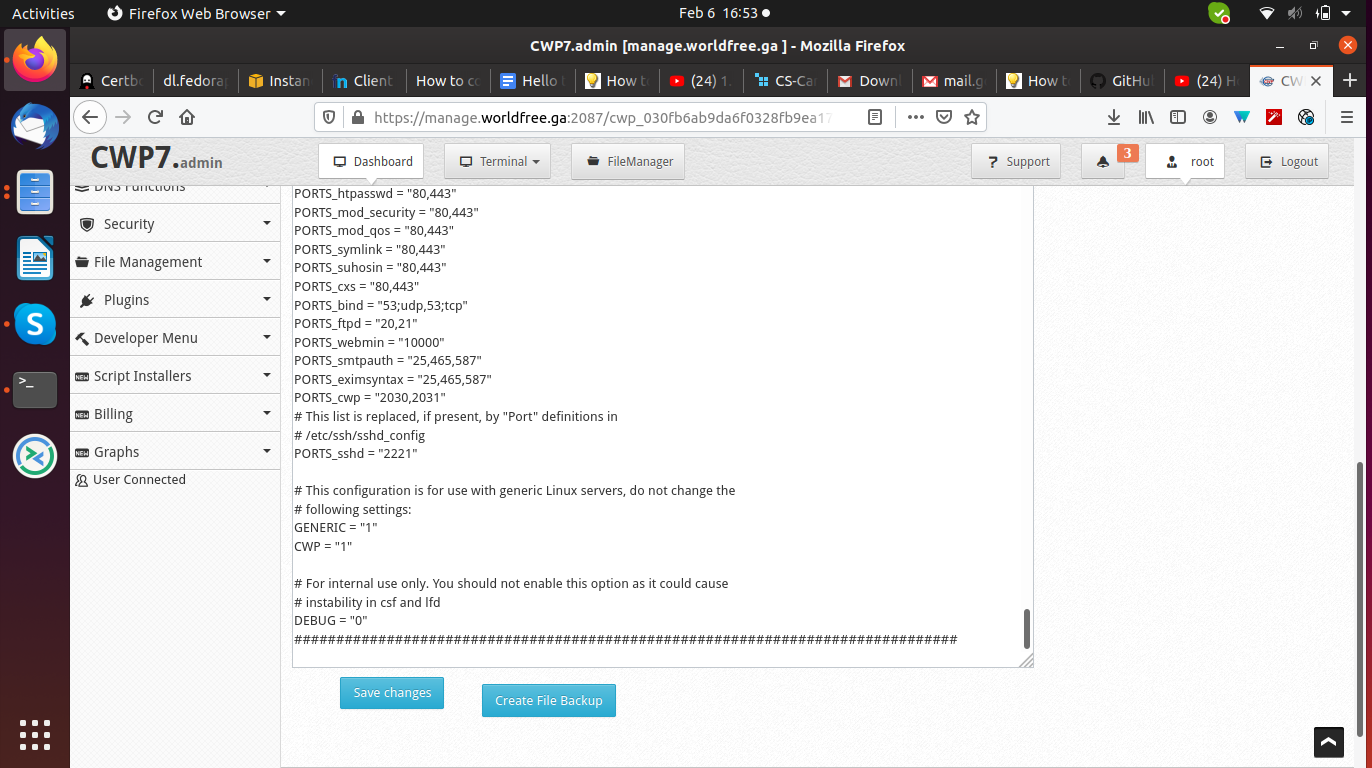
Now edit the configuration file by changing and uncomment port no from 22 to 2221
You can use any port number that is not used with other services and click on save changes.
Now restart the ssh service which is found in the dashboard.
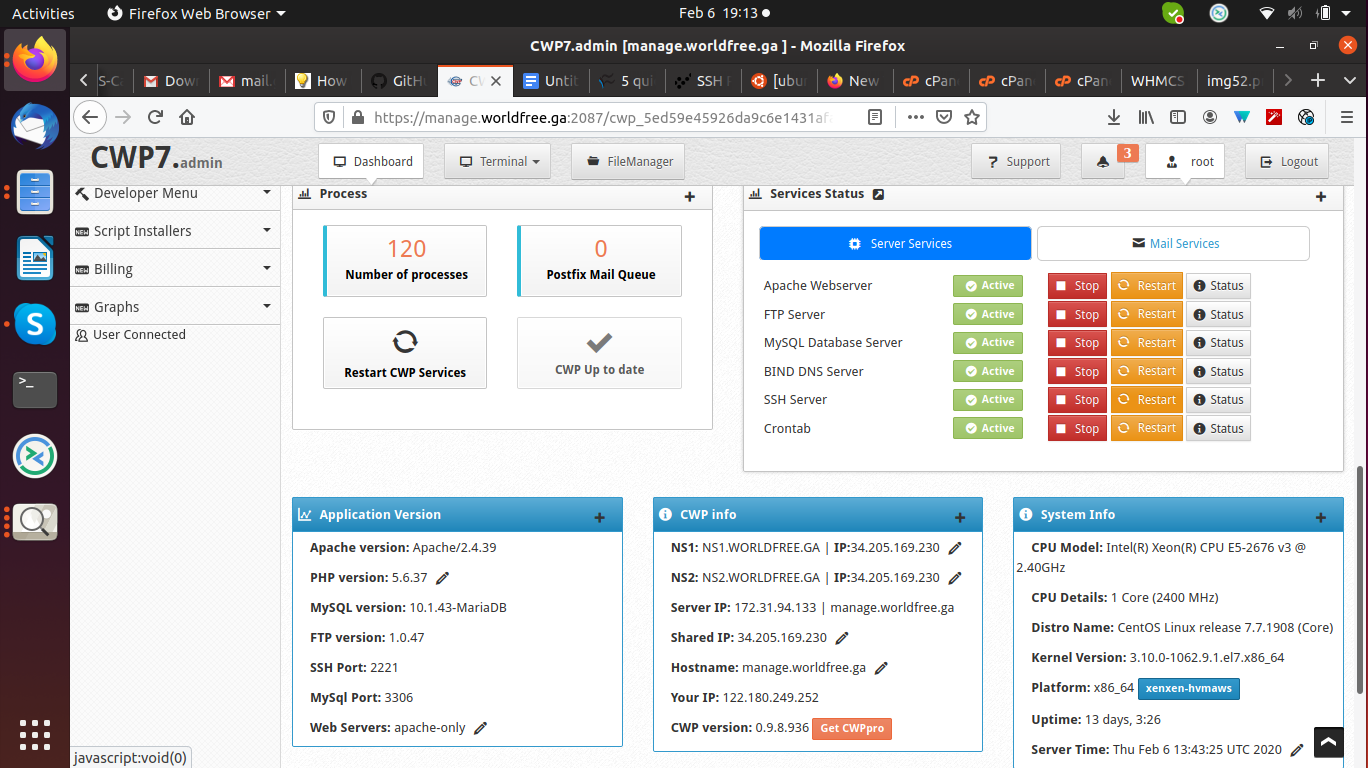
Configure CSF firewall
Changing Port for SSH is not allowed to access until you don’t give the Port number inside the CSF firewall.
To configure it click on security and select CSF firewall, then click on Firewall Configuration and replace in the entry of PORTS_sshd=”22” with PORTS_sshd=”2221” and click on save changes.
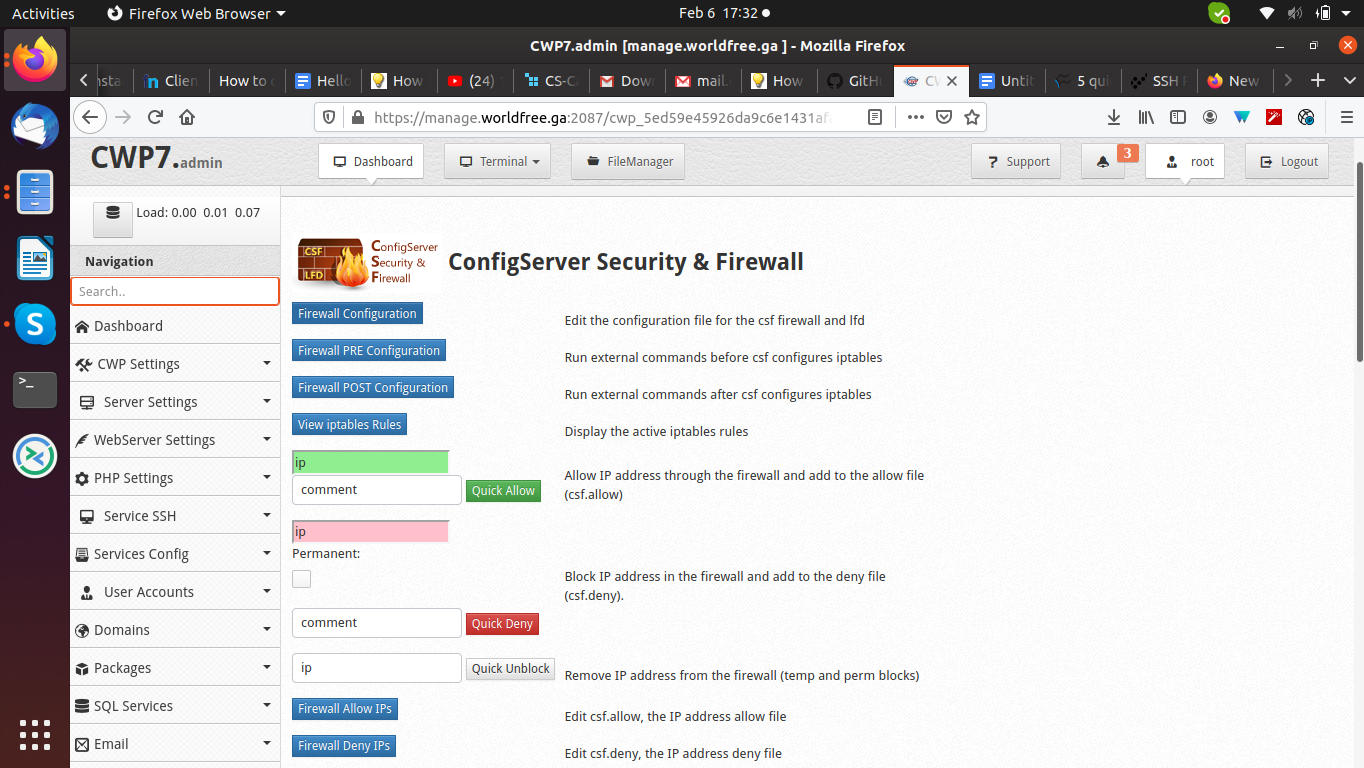
Now restart the Firewall with the Firewall Restart button.
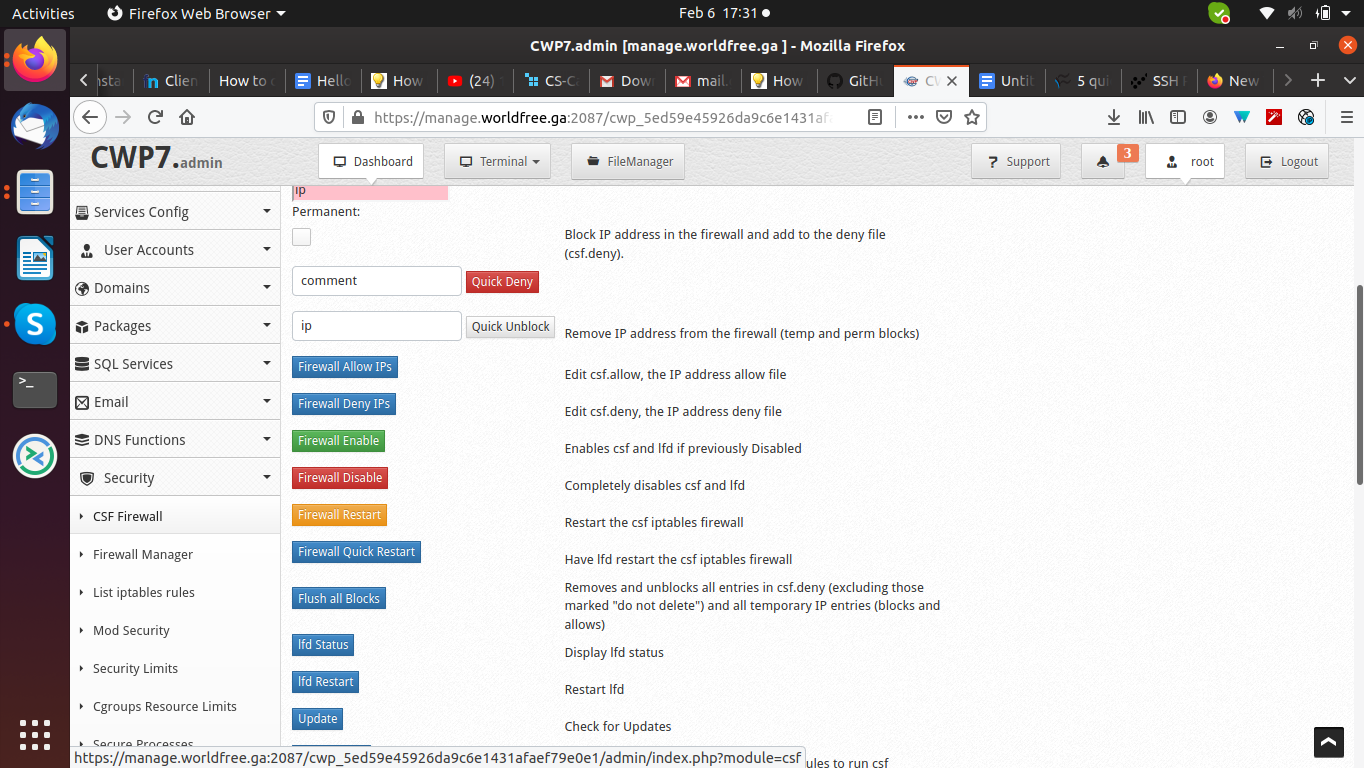
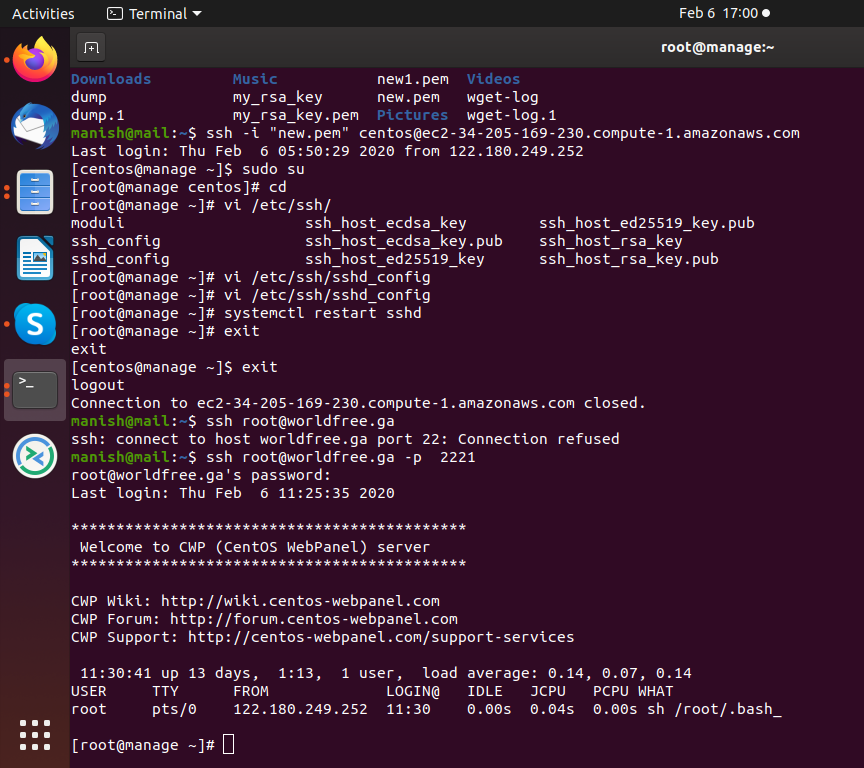
Now test this by using ssh without port change and with the port change you will see the effect.
Other SSH Hardening
1) Limit max authentication attempts
By setting a low threshold for login attempts, you can help prevent brute force attacks. Open the SSH daemon configuration file again with the command:
sudo vi /etc/ssh/sshd_config
Look for the line:
# MaxAuthTries 6
Change that line to:
MaxAuthTries 3
Save and close the file. Restart the SSH server with the command:
sudo systemctl restart sshd
2) Disable empty passwords
There are some system user accounts that are created without passwords. The administrator of a Cheap Linux vps server machine can also create standard users without passwords. Out of the box, SSH is configured so that it doesn’t prevent empty passwords from being allowed. Let’s fix that.
Open the SSH daemon configuration file again with the command:
sudo vi /etc/ssh/sshd_config
Locate the line:
#PermitEmptyPassword no
Change that with:
PermitEmptyPasswords no
Save and close the file. Restart the SSH server with the command:
sudo systemctl restart sshd
CONCLUSION
The above configuration shows how to configure different port numbers for SSH servers and different SSH hardening.
 Register
Register
