Enhancing Security in a Kubernetes Cluster – Refactor Academy
Enhancing Security in a Kubernetes Cluster - Refactor Academy
Introduction

Our client operates a Kubernetes cluster with one frontend server and three backend servers. The client initially faced severe security challenges due to brute force attacks, resulting in server inaccessibility and requiring a complete system rebuild. Additionally, the frontend and backend servers were publicly exposed, leading to frequent data loss issues and OS crashes due to attacks.
Challenges:
Brute Force Attacks: The client’s servers were targets of brute force attacks, compromising server accessibility.
Public IP Exposure: The Kubernetes cluster was configured on public IP addresses, increasing vulnerability.
Inadequate SSH Security The SSH configurations lacked necessary hardening measures.
Lack of Multi-Factor Authentication (2FA): Shell access did not have 2FA, making it easier for attackers to gain unauthorized access.
Frequent OS Crashes: Due to continuous attacks, the servers faced frequent OS crashes.
Frequent Data Loss: Public exposure of frontend and backend servers led to several instances of data loss.
Actions Taken:
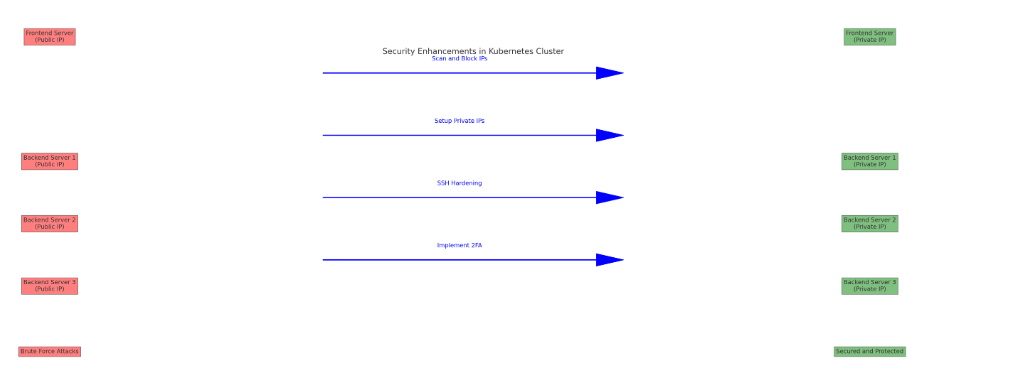
1. Sanning and Blocking Attacker IPs:
a. We performed comprehensive scans on all Virtual Machines (VMs) within the cluster to identify malicious IP addresses.
b. Configured firewall rules and a Web Application Firewall (WAF) to block identified attacker IPs, preventing further unauthorized access attempts.
2. Private VPC Setup:
a. Recognizing the risks associated with public IP exposure, we advised the client’s development team to reconfigure the Kubernetes cluster to operate within a private Virtual Private Cloud (VPC).
b. This setup reduced the attack surface significantly by limiting external access to the cluster.
3. SSH Hardening:
a.Implemented several SSH hardening techniques including:
(i). Disabling root login.
(ii). Restricting SSH access to only essential users.
(iii). Enforcing the use of strong, complex passwords and key-based authentication.
(iv). Changing the default SSH port to reduce automated attack attempts.
b. These measures collectively enhanced the security of SSH access to the servers.
4. Implementing 2FA Policy on Shell Access:
a. Implemented a two-factor authentication (2FA) policy for shell access.
b. This additional layer of security ensured that even if an attacker obtained login credentials, they would still be unable to access the servers without the second authentication factor.
5. OS Crash Mitigation:
a. Addressed the frequent OS crashes by stabilizing the environment through security enhancements and regular updates.
b. Ensured continuous monitoring to detect and address potential vulnerabilities proactively.
6. Additional Security Measures:
a. Network Segmentation:
Separated different parts of the application into isolated network segments to minimize potential attack vectors.
b. Regular Security Audits:
Conducted periodic security audits and penetration testing to identify and mitigate potential vulnerabilities.
c. Automated Backups:
Implemented automated backup solutions to ensure data recovery in case of an attack or system failure.
Here’s the updated diagram illustrating the enhanced security setup in your Kubernetes cluster:
Results:
After implementing the above security measures, the client’s servers were significantly more secure. Key outcomes included:
Reduced Attack Surface: Transitioning the cluster to private IPs and setting up a private VPC substantially decreased exposure to potential external threats.
Enhanced Security Posture: The combination of SSH hardening, 2FA implementation, and additional security measures fortified the overall security of the client’s servers.
Stabilized Systems: Addressing OS crashes and continuous monitoring ensured a stable and reliable system environment.
Conclusion:
Through a strategic combination of IP blocking, infrastructure reconfiguration, SSH hardening, and 2FA implementation, we successfully mitigated the security vulnerabilities faced by our client. These actions not only resolved the immediate issues but also established a robust security framework to protect against future attacks. The client now operates a secure and resilient Kubernetes cluster, with minimized risks of unauthorized access, brute force attacks, OS crashes, and data loss.
This case study underscores the importance of proactive security measures and continuous monitoring to safeguard critical IT infrastructure.
Share
Search Case Studies
AWS Setup and Migration

Skillwinz utilizes the following AWS services:

AWS Cost Optimization:

Gaming and Entertainment

RDS (Amazon Relational Database Service)

Case Studies
- Refactor Academy:
- : India
 Register
Register